Following a year of massive security breaches that targeted some of the world’s largest financial and retail institutions as well as governments and militaries, cyber security startup CyActive today released Cyber Security’s Infamous Five of 2014.
The comprehensive analysis identifies the top five malwares that returned the highest ROI for hackers with the least effort per dollar — achieved by recycling code and using the same methods from previous malware attacks to once again inflict damage. All in all, there were 37 reused components in the top five attacks.
“Cyber Security’s Infamous Five of 2014” and accompanying infographic asks which malware gave cyber criminals the biggest bang for their buck by recycling code and methods from previous malware to gain access to the most coveted cyber targets. (Access full report here.)
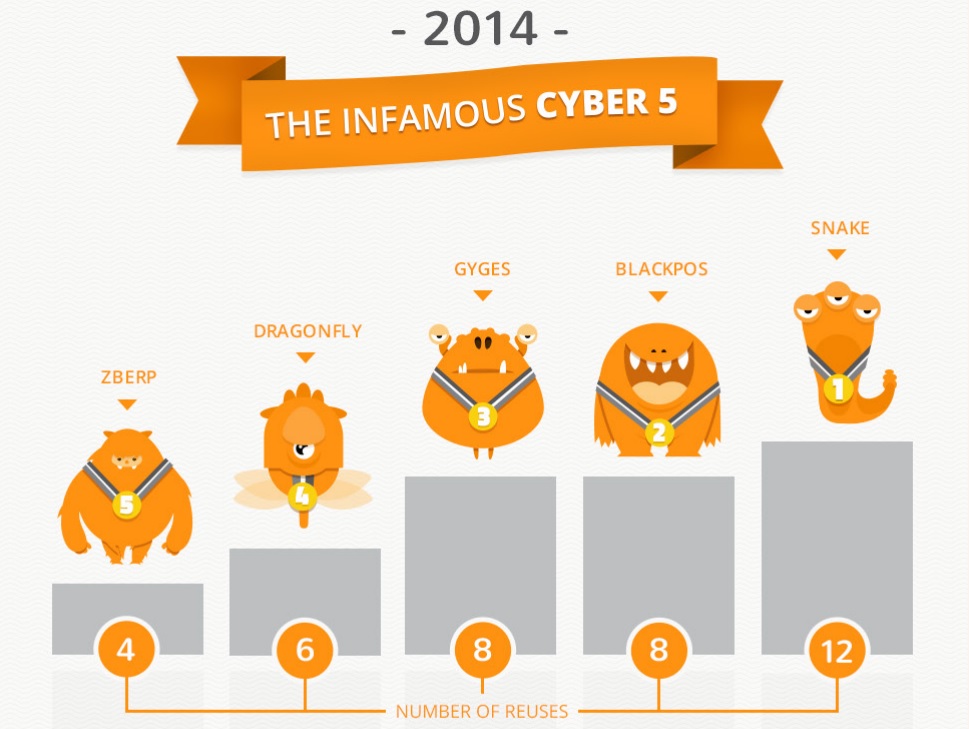
– First place: Snake – Most advanced malware of the group, active the longest (since 2005), and includes 12 reused components
– 2nd place: Black PoS – $200M+ damage, available online for purchase for as little as $1,800, eight recycled components
– 3rd place: Gyges – Government malware gone rogue, reuse of “Government Standard” cyber-stealth tools in cybercrime malware, eight recycled components
– 4th place: Dragonfly – Operated undetected for three years, focused on cyber espionage, eight reused components
– 5th place: ZBerp – Hit 450 financial institutions around the world, four recycled components
While typical rankings of worst security breaches focus on the financial consequences of the most infamous hacks and the headlines generated by them, this report focuses on the degree to which these breaches could have been avoided, and the ease with which recycled malware is used to achieve maximum impact. The analysis reveals a harsh investment asymmetry, wherein the cost and effort of attacks continues to plummet for hackers, while the financial and manpower investments to detect and prevent attacks sharply increases.
“Some of the worst attacks of this year could have been avoided, saving companies, governments and consumers millions of dollars,” said CyActive Co-founder and CEO Liran Tancman.
The analysis, which covers malware that wreaked havoc on financial institutions, retailers and governments, sheds light on the phenomenon of reuse, and how simple it can be for attackers to cause millions of dollars in damage for a mere fraction of the cost of cyber-defense.
“This analysis makes clear how important it is for the cyber security community to focus on predictive, proactive measures to stem the tide of attacks, rather than solely reacting to them,” says Shlomi Boutnaru, CyActive Co-founder and CTO. “Unfortunately, reactive defense remains the common denominator today, despite the overwhelming evidence of reused and recycled components seen in the most notorious attacks.”
About CyActive
CyActive is a predictive cyber security company, which places its clients ahead of potential cyber threats by predicting and preventing future attacks. CyActive has developed an unprecedented ability to automatically forecast the future of malware evolution, based on bio-inspired algorithms and a deep understanding of the black hats’ hacking process. CyActive is the first to offer proactive detection of future malware before it has ever seen the light of day. The resulting solution delivers unparalleled protection to IT and OT devices. CyActive is backed by JVP, Israel’s leading venture capital firm, and by the Venture Capital Unit of Siemens.